Keep machine tools, shop floor data safe from hackers
Keep machine tools, shop floor data safe from hackers
Proactive security measures become even more important as manufacturing software moves into the cloud, machine tool intelligence and automation continue to grow, and the Industrial Internet of Things makes big data an increasingly big deal.
Securing computer systems from intruders should be top priority at homes and businesses alike. Unfortunately, many wait until something goes terribly wrong before taking action.
Proactive security measures become even more important as manufacturing software moves into the cloud, machine tool intelligence and automation continue to grow, and the Industrial Internet of Things makes big data an increasingly big deal.

There are a lot of troublemakers out there, waiting for an opportunity to hack into machine tools, servers and users' computers. Case in point: Nissan manufacturing facility in England hit by cyberattack.
But you just want to make parts. Who has time to worry about a catastrophe that may never happen? Why should you take the trouble to hire an expensive IT geek to sit around watching for that catastrophe—someone who will then enforce a bunch of crazy password rules and internet restrictions on everyone in the company?
Hassle or not, that's exactly what manufacturers should do, at least if they're concerned with machine uptime, intellectual property, data integrity, and loss of the files and software residing on company servers and desktop computers. Can't afford a full-time IT person? Then consider contracting the services of someone like Leonard Jacobs.
Jacobs is president and CEO of Netsecuris Inc., a managed information security services provider in Minneapolis. His customers include smaller companies that recognize today's computing risks but can't justify their own IT staffs and larger firms that need a hand identifying vulnerabilities or continuously monitoring their network traffic.
According to Jacobs, troublemakers attempt to access a network through phishing scams. These are email messages that appear legitimate, but actually contain links to fraudulent websites that trick the recipient into entering sensitive credit card or social security information, for example. Email links may also launch malicious code known as malware, opening back doors for future network reconnaissance. They may secretly install viruses and worms or launch a ransomware attack, whereby the user's computer and data—or possibly a CNC machine tool—is held hostage until a fee is paid.

Posted and easily guessed passwords are asking for trouble.
"By not scanning the contents of a USB flash drive with appropriate antivirus software before plugging it in, people often accidently introduce malware into their computer," he said. "Sometimes people can pick up a virus from visiting websites that might appear legitimate, but are infected with malicious code. We see this all the time while monitoring our customers."
Unacceptable Passwords
Whether you hire a professional or not, Jacobs said regular user training is an important first step in keeping hackers at bay. Teach workers to not click on suspicious links, show them how to construct complex but easy-to-remember passwords and slap the hands of those caught taping a piece of paper with their password written on it to the front of a computer.
"Another frequent mistake is giving people administrative access to their own computer," Jacobs said. "This allows them to inadvertently install software, which increases the risk of a virus. Be sure to keep all computers up to date with security patches and antivirus updates."
Those include the computers inside the shop floor's CNC equipment. Brad Klippstein, controls product specialist at Okuma America Corp., Charlotte, N.C., said regular patching is something many shops overlook, especially those without an IT department. However, it is an important part of any preventative-maintenance program.
Patching is just a small part of the network security picture, however. Like most large organizations, Okuma is the target of frequent digital attacks, which is why Klippstein recommends a robust firewall.
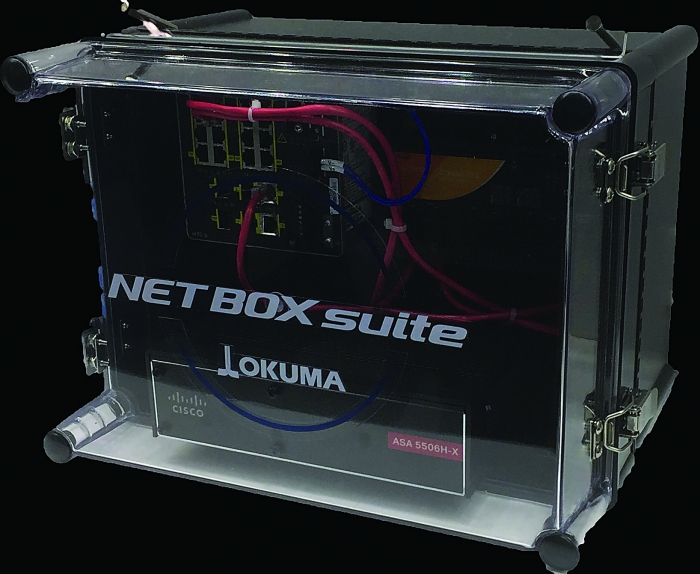
Hardware devices like the Okuma NETBOX are only part of a sound network security strategy. User training, strong password policies and other good IT practices are also important. Image courtesy of Okuma America.
"Even without some of the hardware security devices introduced recently," Klippstein said, "it's quite feasible to configure the network in a way that isolates the CNCs from the rest of the company. All that's needed is to set rules for what types of information are allowed or not allowed to move through the different ports in the firewall. Then make sure the network routers and switches are secured with strong passwords. We've been doing it for years."
Klippstein noted system security also involves establishing an intranet, or VLAN (virtual local area network), a network inside of a network that is isolated from the outside world.
Simplifying Security
"If a hacker or other person with malicious intent gains access to an unprotected port," Klippstein said, "they can 'spiderweb' out to any device on the network, including the machine controls, from which they can launch attacks on other devices. Using a separate LAN eliminates that risk."
In 2016, Okuma introduced the Net Box suites, tools to simplify this aspect of network security. According to the company, these tools block unauthorized access to machine networks from external cyberattacks. Klippstein said the Net Box is an industrial ethernet switch that works with the MTConnect protocol and supports Okuma P-series controls, as well as those on legacy machine tools, even ones without network capabilities.

Data centers like this one offer hosting and co-location services, providing uptime and physical security generally unachievable with on-premise hardware.
There are other network tools on the market. Mazak Corp. offers a similar product, the SmartBox. Neil
Desrosiers, applications engineer and MTConnect specialist at Mazak, Florence, Ky., said, "We teamed up with Cisco and said, 'Hey, we're doing monitoring and analytics and machine utilization, but we see a big security pushback from IT departments whenever we talk about pushing this data past the office door and into the enterprise management systems, where decisions can be made.' "
There is an increased call for machine-to-machine communications, and the integration of robots and metrology systems into manufacturing cells, as well as potentially massive amounts of data flowing from IIoT-based sensing devices in machine tools. Therefore, shops need a flexible but secure way to connect equipment. "You can't just lock things down," Desrosiers said.
Living on the Edge
For those who think such protective measures are overkill for mom-and-pop shops, think again. Desrosiers teaches a quarterly MTConnect boot camp, where he regularly hears horror stories from attendees about how their shops were hacked. "Companies don't like to advertise when they get a virus or to tell anyone that half the factory was shut down because of malware brought in on someone's laptop, but it happens," he said. "That's why machine protection is so important."
And it's only going to become more important. As machine tool capabilities grow, an increasing amount of information will stream to servers and cloud-based systems for analysis and decision-making—possibly flooding the network with enough data to cause a traffic jam.
Desrosiers said he's worked with customers who were experiencing similar problems. He solved them with the SmartBox, which can perform "on edge" computing within the device's Linux core and then deliver a condensed version of the results to whatever server or software system is asking for them, greatly reducing network traffic.
Some shop owners might groan about the approximate $4,000 price tag per SmartBox. Depending on the amount of data being pulled, however, each device can handle up to 10 machines. And because each SmartBox creates its own VLAN, a problem on one group of machines will not affect those connected to a different device. "Every time you implement a SmartBox, you add a layer of security to your network," Desrosiers said.
Co-location Considerations
Some manufacturers choose to move at least some of their servers and software systems—and the management of those IT assets—off-site, thus handing responsibility for potential security problems to others. Although partnering with hosting and co-location service providers offers distinct advantages over on-premise computing, it's not as simple as saying, "Here, you guys deal with it."

The Mazak SmartBox is a managed industrial switch that provides not only network security but also analytics and machine monitoring. Image courtesy of Mazak.
Martin Wielomski, global manager of products and evangelism at PhoenixNAP LLC, a global IT service provider based in Phoenix, said companies face a number of risks with on-premise server infrastructure. These risks include:
- data unavailability because of hardware failures;
- missing or poorly defined backup and disaster recovery strategies;
- lack of spare hardware components, such as power supplies and hard drives;
- insufficient network redundancy or capacity; and
- absence of a sound distributed-denial-of-service protection plan.
It's enough to keep any shop owner awake at night.
"There's also the physical security of the hardware to consider," Wielomski said. "Things like fire protection and electrical fluctuations, and unauthorized access to the hardware in order to either directly harvest information or for purposes of malicious software installation. These and other risks are mitigated by working with an infrastructure-as-a-service provider."
This partnership typically takes one of two forms. Co-location means moving existing hardware to a multitenant data center, where it remains under the management of the customer's IT staff. The service provider is responsible only for the facility and its operations.
A hosted solution is more comprehensive. In this case, the hardware (and, in some cases, software) is essentially rented from the service provider. Maintenance and uptime are assured through a service level agreement, any breach of which incurs financial penalties to the provider.
Each approach has its pros and cons, but for those with an IT staff, either may bring heartburn due to a perceived loss of control.
"Outsourcing allows companies to focus on their key business elements and rely on partners to support IT activities," Wielomski said. "This does not mean getting rid of your IT staff, but it does allow them to change their daily focus to activities that improve business operations, customer experience and the bottom line. In other words, they will be tasked with innovation and optimization of IT-related business components and processes rather than keeping busy with system performance and availability."







